From Admin to Kernel: One Year, One Driver, Zero Attention
Introduction & Motivation
My little journey started with an exploration of third-party drivers to uncover possible vulnerabilities. While using the System Informer tool to review the drivers active on my system, I discovered DellInstrumentation.sys.
For over a year, DellInstrumentation.sys has remained under the radar, leaving a potential privilege escalation vulnerability from admin to kernel unexamined by the security community. This isn’t the first time Dell drivers have been vulnerable; in 2021, CVE-2021-21551 exposed privilege escalation flaws in Dell’s BIOS driver, affecting millions of DELL devices.
Deja Vu Moment
After beginning to reverse-engineer DellInstrumentation.sys, I had a strong sense of déjà vu. Not long ago, I analyzed DBUtilDrv2.sys (version 2.7), and the two drivers share many similarities. Both drivers utilize nearly identical IOCTLs and are KMDF-based. However, DBUtilDrv2.sys is already known as a vulnerable driver. This raised the possibility that DellInstrumentation.sys might suffer from the same weaknesses, prompting me to dig deeper into its security flaws.
Key Differences Between DellInstrumentation.sys and DBUtilDrv2.sys
While DellInstrumentation.sys and DBUtilDrv2.sys share many similarities, several important differences stand out:
-
Model-Specific Registers (MSR) Support: Unlike
DBUtilDrv2.sys,DellInstrumentation.sysincludes functionality for reading Model-Specific Registers.
IOCTL:0x9B0C1E40.
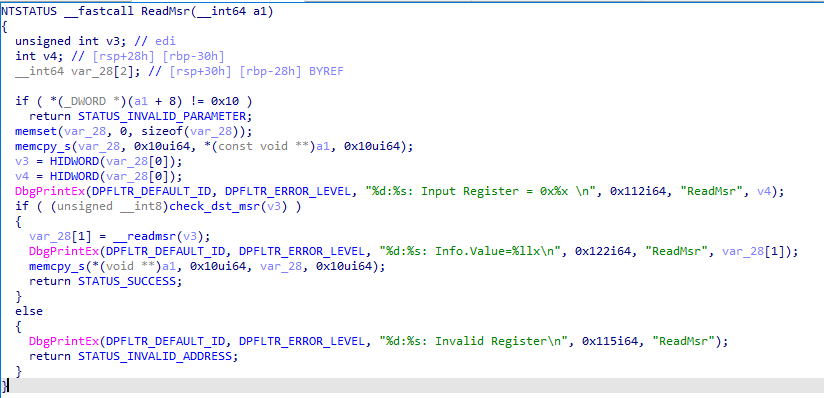
-
PCI Access: Unlike
DBUtilDrv2.sys,DellInstrumentation.sysincludes functionality for accessing PCI devices.
IOCTL:0x9B0C1F48and0x9B0C1F4C.
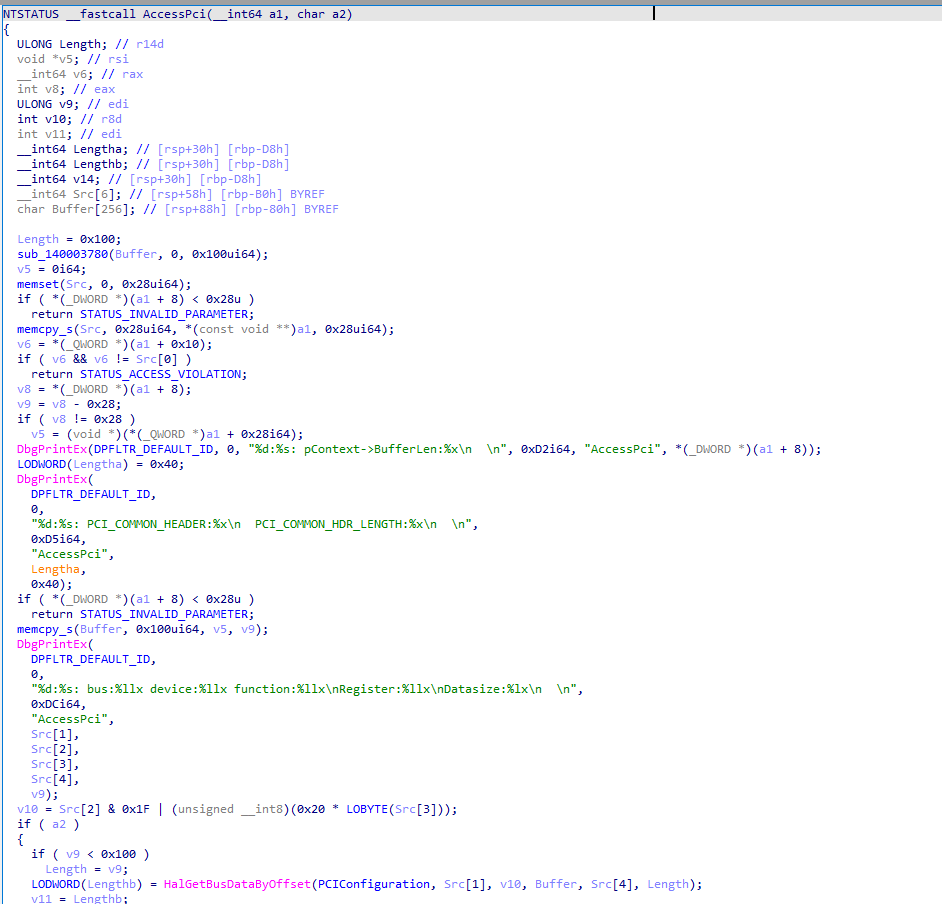
-
DbgPrintEx Usage:
DellInstrumentation.sysmakes extensive use of DbgPrintEx calls, which include function names and parameter names, providing deeper insight into the driver’s internal operations and functionality. -
Symbolic Link Name: The symbolic link for
DellInstrumentation.sysis namedDell_Instrumentation, distinguishing it from the one used byDBUtilDrv2.sys(DBUtil_2_5).
Proof of Concept
The PoC is very similar to CVE-2021-21551 PoC, you can find my code on GitHub.
Thanks
Kasif Dekel, mathisvickie, Paolo Stagno (aka VoidSec), Takahiro Haruyama.
OpenSecurityTraining2 (OST2) ![]() .
.
Resources & References
- CVE-2021-21551- Hundreds Of Millions Of Dell Computers At Risk Due to Multiple BIOS Driver Privilege Escalation Flaws
- Reverse Engineering & Exploiting Dell CVE-2021-21551
- Exploit Development: CVE-2021-21551 - Dell ‘dbutil_2_3.sys’ Kernel Exploit Writeup
- Simple PoC for exploiting CVE-2021-21551 for LPE by spawning system cmd
- Hunting Vulnerable Kernel Drivers